Add Page Based Security Using Authorized Roles"
| Line 13: | Line 13: | ||
===Configuration=== | ===Configuration=== | ||
| − | Application specific configuration for Spring security is generally specified within Spring bean configuration file or altogether in a separate xml file. But for Spring Security to discover those configuration we need to add certain configuration into web.xml as shown below | + | In addition to the basic ZK Spring configuration as described earlier [[ZK_Spring_Essentials/Getting_Started_with_ZK_Spring/Setting_Up_ZK_Spring|here]] we will need following onfiguration for Spring Security. Application specific configuration for Spring security is generally specified within Spring bean configuration file or altogether in a separate xml file. But for Spring Security to discover those configuration we need to add certain configuration into web.xml as shown below |
<source lang="xml"> | <source lang="xml"> | ||
<context-param> | <context-param> | ||
| Line 112: | Line 112: | ||
The most important part of login.zul page is the login form that must be configured to work with Spring Security. The name of input textboxes for user name and password must match <code>j_username</code> and <code>j-password</code> as specified by Spring Security. Also the form must be submitted to <code>j_spring_security_check</code> action url. | The most important part of login.zul page is the login form that must be configured to work with Spring Security. The name of input textboxes for user name and password must match <code>j_username</code> and <code>j-password</code> as specified by Spring Security. Also the form must be submitted to <code>j_spring_security_check</code> action url. | ||
| − | |||
=Version History= | =Version History= | ||
Revision as of 01:23, 23 February 2011
Purpose
Secure ZK ZUML pages with Authorized roles
Example
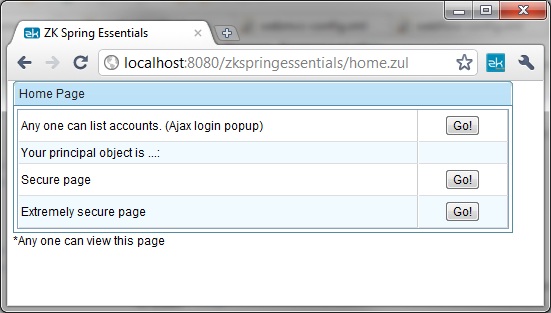
This Example is borrowed from the standard Spring Security tutorial sample and has been modified to work with ZK using ZK Spring Security. You can download the example codes from ZK Spring Essentials Google Code source repository here. You can see this example in action by deploying ZK Spring Essentials web archive and hitting example home page at http://localhost:8080/zkspringessentials/home.zul and you will see following screen. home.zul page is configured to be accessible to anyone.
This table lists links to different pages that users can visit. Two more pages as listed in the bottom two rows of above table that can be visited by clicking "Go" buttons, secure/index.jsp and secure/extreme/index.jsp are configured to be accessible to only those users that have certain authorized roles. If users click on these "Go" buttons, first Spring security checks if they are logged in or not. If they aren't logged in they will be presented a login page. On successful login Spring Security will also verify if they have the specific roles assigned to them that will authorize access to those pages. If they have been assigned those authorized roles users will be redirected to related pages or else they will be shown access denied page.
Lets dig into the configuration to see how we secure these pages with authorized roles
Configuration
In addition to the basic ZK Spring configuration as described earlier here we will need following onfiguration for Spring Security. Application specific configuration for Spring security is generally specified within Spring bean configuration file or altogether in a separate xml file. But for Spring Security to discover those configuration we need to add certain configuration into web.xml as shown below
<context-param>
<param-name>contextConfigLocation</param-name>
<param-value>
/WEB-INF/applicationContext-security.xml
</param-value>
</context-param>
<listener>
<listener-class>org.springframework.web.context.ContextLoaderListener</listener-class>
</listener>
<filter>
<filter-name>springSecurityFilterChain</filter-name>
<filter-class>org.springframework.web.filter.DelegatingFilterProxy</filter-class>
</filter>
<filter-mapping>
<filter-name>springSecurityFilterChain</filter-name>
<url-pattern>/*</url-pattern>
</filter-mapping>
Here org.springframework.web.context.ContextLoaderListener is responsible for loading the Spring Security configurations and org.springframework.web.filter.DelegatingFilterProxy is the main entry point of Spring Security framework.
Secure pages
Now lets take a look at our example specific configuration that enables role based security to certain pages as described above. it is defined in applicationContext-security.xml file as shown below.
<http auto-config="true">
<intercept-url pattern="/secure/extreme/**" access="ROLE_SUPERVISOR"/>
<intercept-url pattern="/secure/**" access="ROLE_USER" />
<intercept-url pattern="/**" access="IS_AUTHENTICATED_ANONYMOUSLY" />
<form-login login-page="/login.zul"
authentication-failure-url="/login.zul?login_error=1" />
<logout logout-success-url="/home.zul"/>
</http>
<intercept-url /> element in above configuration is used to define what role user needs to have in order to access certain page. Page or a pattern that identifies a group of pages is configured using attribute attribute.
Users and roles
In real world application user credentials and their assigned roles will be stored in a database or handled by other some other protocol/service such as LDAP/CAS. For simplicity we will define a group of user credentials and their roles in the configuration file
<authentication-manager>
<authentication-provider>
<password-encoder hash="md5" />
<user-service>
<user name="rod" password="a564de63c2d0da68cf47586ee05984d7"
authorities="ROLE_SUPERVISOR, ROLE_USER, ROLE_TELLER" />
<user name="dianne" password="65d15fe9156f9c4bbffd98085992a44e"
authorities="ROLE_USER,ROLE_TELLER" />
<user name="scott" password="2b58af6dddbd072ed27ffc86725d7d3a"
authorities="ROLE_USER" />
<user name="peter" password="22b5c9accc6e1ba628cedc63a72d57f8"
authorities="ROLE_USER" />
</user-service>
</authentication-provider>
</authentication-manager>
Custom login page
If user isn't logged in Spring security presents a default login page to the user to enter his credentials. You can customize this to present a custom login page instead. In this example we are using a custom login page i.e. login.zul ZUML page and it is configured using <form-login/> element's login-page attribute. On wrong credentials we also configure Spring Security to present the same login page again and also pass an indicator of failure login_error=1 that we use to display certain login failure message to the user and ask to re-enter correct credentials.
<form-login login-page="/login.zul"
authentication-failure-url="/login.zul?login_error=1" />
<logout logout-success-url="/home.zul"/>
As you can see above we have also configured a logout-success-url to home.zul page instead of default "/" path. Now lets take a look at login page source.
<?page id="testZul" title="CUSTOM ZK + SPRING SECURITY LOGIN"?>
<window id="loginwin" title="CUSTOM ZK + SPRING SECURITY LOGIN" border="normal" width="500px">
<!-- this form-login-page form is also used as the
form-error-page to ask for a login again. -->
<html style="color:red" if="${not empty param.login_error}">
<![CDATA[
Your login attempt was not successful, try again.<br/><br/>
Reason: ${SPRING_SECURITY_LAST_EXCEPTION.message}
]]>
</html>
<groupbox>
<caption>Login</caption>
<h:form id="f" name="f" action="j_spring_security_check" method="POST"
xmlns:h="http://www.w3.org/1999/xhtml">
<grid>
<rows>
<row>User: <textbox id="u" name="j_username"/></row>
<row>Password: <textbox id="p" type="password" name="j_password"/></row>
<row><checkbox id="r" name="_spring_security_remember_me"/>Don't ask for my password for two weeks</row>
<row spans="2"><hbox>
<h:input type="submit" value="Submit Query"/>
<h:input type="reset" value="Reset"/>
</hbox></row>
</rows>
</grid>
</h:form>
</groupbox>
</window>
The most important part of login.zul page is the login form that must be configured to work with Spring Security. The name of input textboxes for user name and password must match j_username and j-password as specified by Spring Security. Also the form must be submitted to j_spring_security_check action url.
Version History
| Version | Date | Content |
|---|---|---|